Posted by John Beuke
This article describes common security risks in network print infrastructures and explains how to secure your environment and reduce or eliminate the many vulnerabilities associated with print servers and multifunction devices (MFDs) or printers.
Background
In July 2018, the Ponemon Institute released 2018 Cost of Data Breach Study: Global Overview, its thirteenth annual study on the cost of data-breach incidents. The research showed the increasing upward trend in the global costs of data breaches. For example, the average total cost of a data breach was estimated to be $3.86 million.
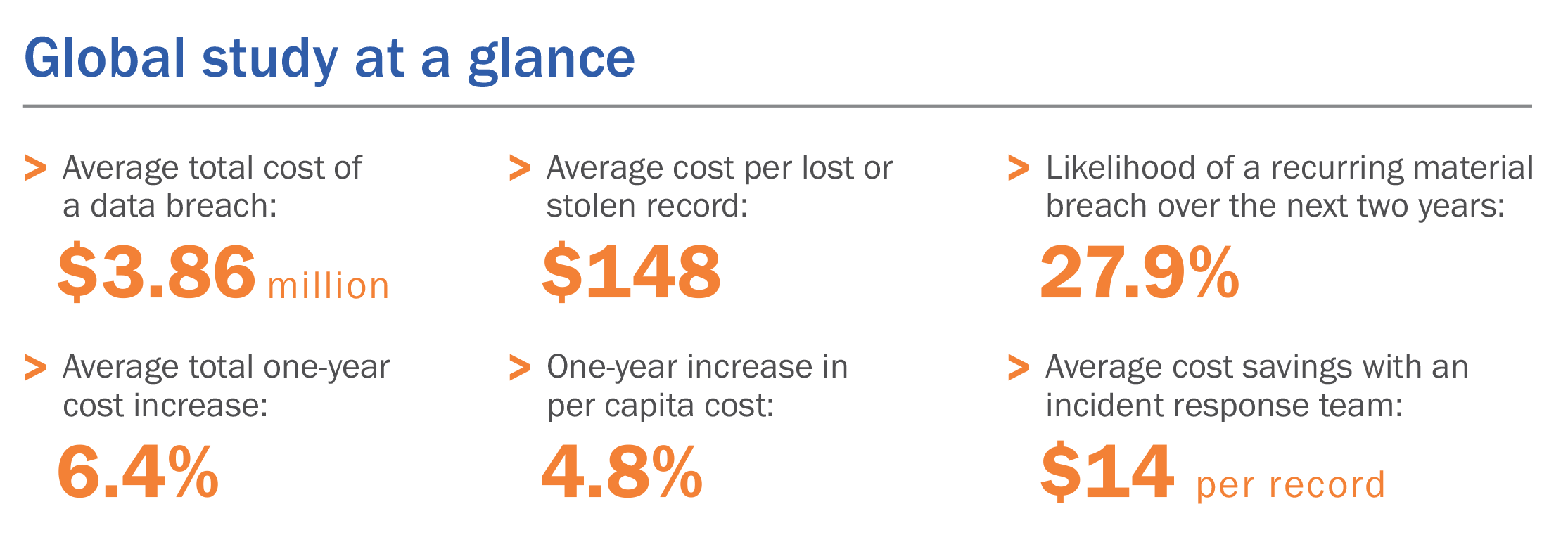
The causes of a data breach can be narrowed to two general types: intentional and accidental. Intentional breaches occur when a malicious actor, either inside or outside the organization, gains access to sensitive data and exploits it. An accidental breach, which is more common, occurs when the actor mistakenly releases the information.
Given the many recent advances in cybersecurity, one might assume that the prevention of both types of data breaches is improving. Unfortunately, the increasing complexity of technology and the rate at which it is evolving means the opposite is true.
Creating a Secure Print Infrastructure
Every time a document or form is copied or printed, sensitive data can be accidentally exposed or intentionally compromised. It is our recommendation that the following steps be implemented to create a more secure print infrastructure.
Eliminate single points of vulnerability
Most print servers and print-management software hold jobs waiting to be printed in a centralized location. Removing this central repository reduces the risk of a single-vector attack. Documents should instead be held locally at the user’s workstation until the print job is executed at the printer. This distributes any associated risk over many attack vectors; any exposure would therefore likely be limited to the user’s local workstation and not the entire enterprise.
Eliminate single points of failure
Should the print server(s) or communication with these servers fail for any reason, printing comes to a standstill until the issue is resolved. This results in lost productivity for users as well as for IT administrators, who are forced to abandon other priorities and redirect their focus on restoring print capabilities.
Our recommendation for this issue, as well as the single point of vulnerability noted above, is to eliminate print servers altogether by transitioning to a centrally managed direct-IP printing model, such as the one that PrinterLogic offers with its advanced print-management solution.
Centrally audit print activity
Centrally auditing print activity involves establishing a system whereby printers store information of their respective print-job history in a common database. In the event of a breach, this database would facilitate the identification of any printing device and user affected by the breach.
PrinterLogic’s print-management solution has built-in print auditing capabilities. This feature comprehensively tracks all print data across the print network by default enabling administrators to pinpoint print-related network events that involve a specific user or device.
Implement secure print release
It’s estimated that 15-20 percent of printed documents end up abandoned and are left in the print tray. This means anyone can walk by and gain access to sensitive data before it is retrieved by the owner of the document. By contrast, secure print release employs a methodology in which only the user who printed the job is authorized to release (i.e., execute) the job.
We recommend implementing secure print release functionality as found in PrinterLogic’s print-management solution. This feature enables users to print and retrieve their documents securely and conveniently using common authorization protocols.
Enforce role-based access control
It is critical from a security perspective that granularized access control be applied to multifunction devices (MFDs) and printers. This means that the printing devices must likewise support the restriction of features and capabilities of an authenticated user on the basis of group policy membership.
We recommend the implementation of strict role-based access control alongside print-management software and printing hardware (e.g., MFDs, printers) that natively support this practice.
Apply cryptographic standards
All print data must be encrypted to ensure that any compromised data will be difficult to access. These encryption standards include the federal government’s FIPS 140-2 standard, along with other standards used in encryption services.
The PrinterLogic solution is compliant with HSPD-12 and compliance-pending with the FIPS 140-2 standard. We expect to receive compliance verification by the end of 2018. PrinterLogic will meet the security requirements for cryptologic modules used by the U.S. military. We use TLS V1.2 for all print management and related data in motion (DIM) between workstations and the PrinterLogic Web Stack (formerly Printer Installer) Server.
Supported printers are configured to utilize FIPS 140-2 accredited Open SSL/TLS FIPS Object Modules—including AES and RSA for data at rest and data in motion. Data at rest (DAR) is protected using the Windows operating system and not the PrinterLogic software.
Digitally sign print jobs to ensure document integrity
For true end-to-end print security, we recommend that all print jobs are digitally signed at the point of print. PrinterLogic’s advanced software validates the print job by comparing hash values and the digital certificate obtained from the smart card prior to releasing the job.
Conclusion
Given the increasing cost of preventable data breaches, it is vital for organizations to take immediate and active steps to minimize risk by limiting and protecting potential access points on their print network. The costs of penalties and settlements, as well as indirect repercussions that stem from failing to secure printers, can be significant, even catastrophic.
PrinterLogic provides a single integrated software package that incorporates device-agnostic printer and driver management as well as secure printing with CAC/PIV authentication. This solution facilitates printing compliance by adding a layer of security and control that uses robust, automated security protocols that cannot be circumvented. As a result, PrinterLogic reduces the risks inherent in existing print infrastructures, corrects non-compliance, and helps companies and agencies avoid the penalties and other costs of data breaches.
To see for yourself how PrinterLogic’s next-generation print management solution can provide your organization with a secure print infrastructure that is also highly flexible and infinitely scalable, sign up for the free 30-day demo today.
