THE ORIGIN STORY
What Is PrintNightmare?
To Put It Technically
“A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
– CVE-2021-34527
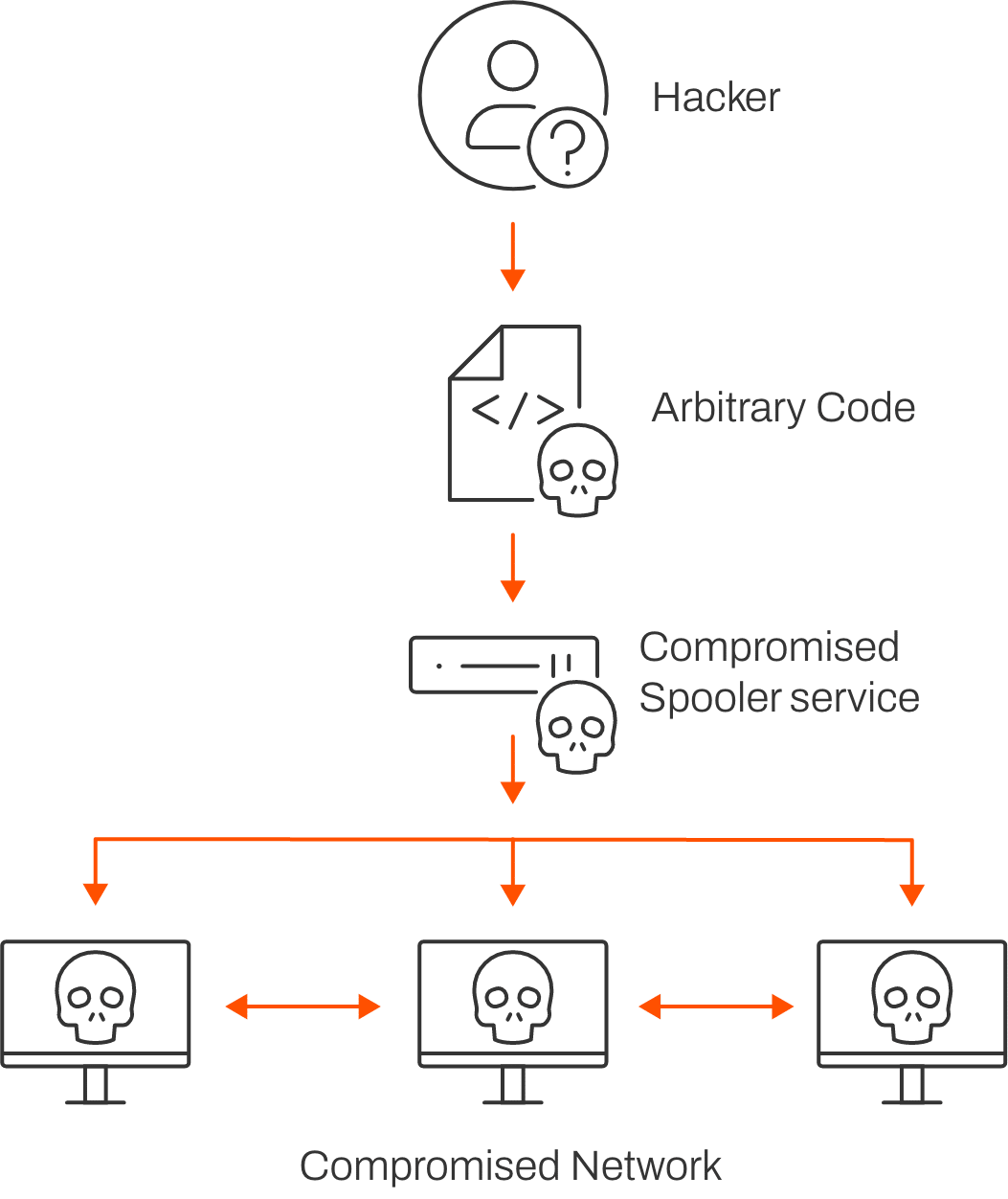
To Sum It Up
This pesky vulnerability is exposed through specific inbound Remote Procedure Calls (RPC), which fail to properly restrict the administration of printers and related drivers. An attacker could then execute arbitrary code on a vulnerable system, allowing them free access to attack all of your connected devices. That means your whole network is vulnerable—not exactly a daydream.

THE SAGA CONTINUES
Return of the PrintNightmare
Attack of the Patches
When the initial vulnerability was found, patches were released. That’s good news for cutting off potential costly breaches. Unfortunately, more potential problems were discovered from these fixes, which led to additional patches that removed point and print capability for users and introduced changes to User Access Control (UAC).
A Neverending Story
You’re likely back to entering Admin Credentials for every user trying to print from a computer that needs new print drivers installed or updated. No more self-installs for your users! As an added bonus, your company (like many others) is probably now looking to invest in print security and other ways to keep your print servers secure.

The Terrifying Truth
SERVERLESS SAVES THE DAY
A Complete PrintNightmare Fix
Be the Hero
Well, the fix you’ve been looking for is here. With Vasion Print (formerly PrinterLogic), you can eliminate your print servers, terminating PrintNightmare and other spooler errors—permanently. No more messy patches or costly print disruptions consuming your time and resources! Implementing a serverless print infrastructure with Vasion Print means eliminating a common attack vector and centrally managing direct IP printing from a single pane of glass.
Empower your end users with a Point and Print alternative through our self-service portal. Users are able to install and update their own printers without needing admin credentials. This way you and your IT team can get back to the important work of keeping your company running smoothly while our highly available, cloud print management solution keeps your print data and network protected.
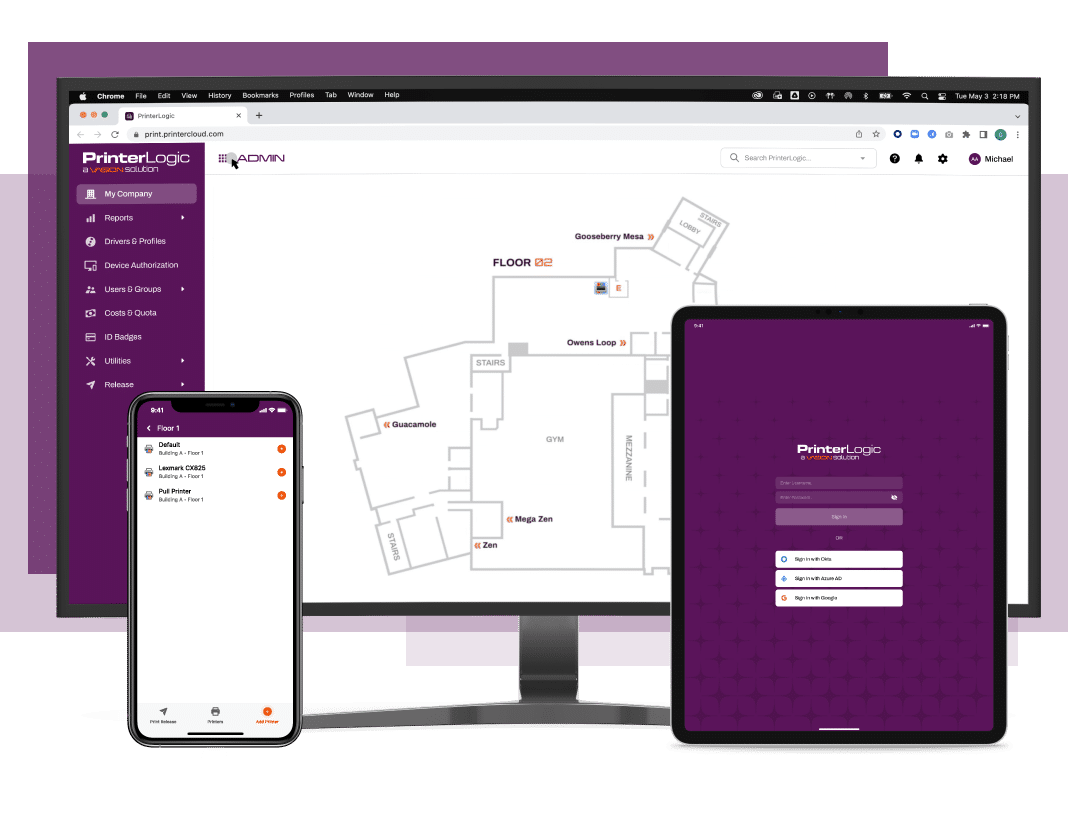
A SATISFYING CONCLUSION
No More PrintNightmares
A Happy Ending
See how centrally-managed direct IP printing takes print spoolers out of the picture and gives you and your users more control of your print environment. That means no more vulnerabilities keeping you up at night.
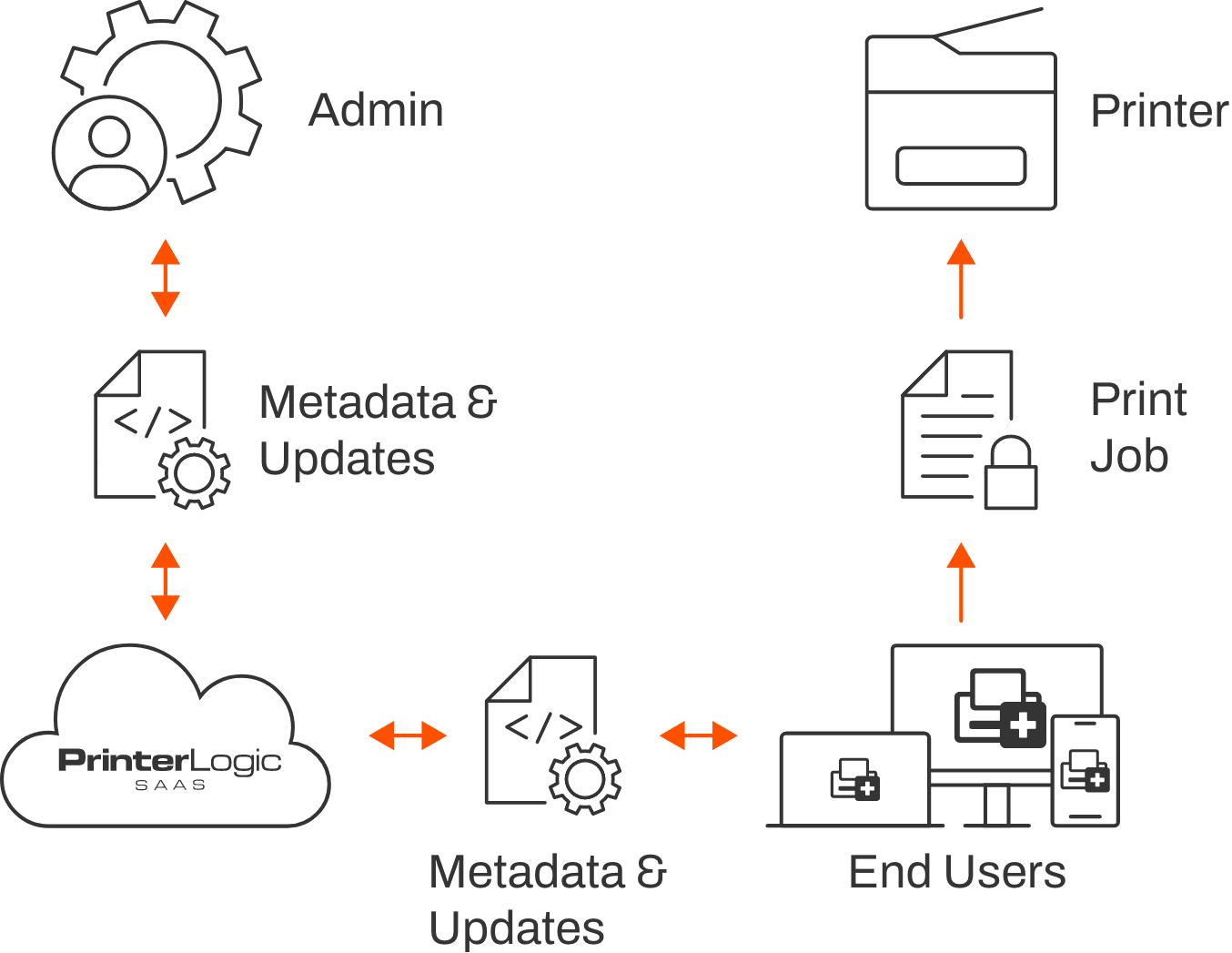
Our Direct IP Infrastructure

Eliminates
Reduces attack surfaces by eliminating print servers to protect against current and future issues.

Decentralizes
Removes a centralized
exploration point where hackers can access encrypted data.

Segments
Segments and segregates your network services to better secure your data and protect against breaches.

Restricts
Decreases risk
with access and authentication restricted to the workstation level.
TESTIMONIAL
Thanks to [Vasion Print (formerly PrinterLogic)], we were saved from PrintNightmare vulnerability."
It’s Time To Wake Up
Vasion Print is the most secure way to protect your company from
PrintNightmare and all other print server vulnerabilities. Wake up from your PrintNightmare today with a demo of Vasion Print.
NEED MORE?
Ask Reddit
Still not sure if serverless printing is right for you? Check out what Reddit has to say.
Frequently Asked Questions
What is the PrintNightmare vulnerability?
PrintNightmare, made public in 2021, was a remote code execution vulnerability that allowed unauthorized users to execute code without admin credentials. They were able to do so because the Windows Print Spooler was exposed through specific inbound Remote Procedure Calls.
Is the Microsoft PrintNightmare fixed?
Yes and no! Microsoft has released several patches that fix the initial execution vulnerability. However, the patches led to other problems. This includes changes to the User Account Control (UAC) prompts, meaning that many users can no longer make any changes without admin credentials.
What is the Microsoft update for PrintNightmare?
You can find the latest patches and updates for PrintNightmare and other Microsoft Spooler vulnerabilities on their MSRC site. Note that PrintNightmare is distinct from other spooler issues such as PrintDemon, SpoolFool, and others. Make sure all patches are up to date to avoid any issues.
Who does PrintNightmare affect?
Anyone running Windows Print Spooler on a print server should make sure that the patches have been implemented on their system
How do I fully patch the PrintNightmare vulnerability?
First, make sure all currently released patches have been installed. This will keep your network secure for now. But the best way to avoid this vulnerability and other spooler errors in the future is to eliminate your print servers entirely.
Are Vasion Print customers affected by PrintNightmare?
No! Our serverless printing platform means that our customers are insulated from print spooler errors, and our segmented infrastructure means that any end devices that do get compromised cannot be used to access other network data.
PrintNightmare 2.0: 4 ways to avoid a recurring bad dream
Discover how to avoid another PrintNightmare with this in-depth blog discussing Vasion Print and spooler vulnerabilities.